| Россия, Санкт-Петербург |
Networks and the Internet
Wireless LANs
An obvious problem with Ethernet is that you need a cable. As more and more machines are installed, the cabling can become a nightmare. It's particularly inconvenient for laptops: the network cable restricts where you can use the machine.
Wireless network cards have been around for some time, but in the last few years they have become particularly popular. Modern cards are built around the IEEE 802.11 series of standards.
They are usually PCMCIA (PC Card) cards, though some PCI cards are also available. Currently you're liable to come across the following kinds of cards:
- 802.11 FHSS (Frequency Hopping Spread Spectrum)cards, which run at up to 2 Mb/s. These are now obsolete, but FreeBSD still supports the WebGear Aviator card with the ray driver.
- 802.11 DSSS (Discrete Sequence Spread Spectrum)cards, which also run at up to 2 Mb/s. These are also obsolete.
- 802.11b DSSS cards, which run at up to 11 Mb/s. They can interoperate with the slower 802.11 DSSS cards, but not with FHSS cards.
- 802.11a cards, which run at 54 Mb/s. They use a modulation called Orthogonal Frequency Division Multiplexing or OFDM, and run in the 5 GHz band. They are not compatible with older cards. At the time of writing, they have not achieved significant market penetration. FreeBSD does not support them yet, though that may have changed by the time you read this.
- 802.11g cards are the newest. Like 802.11a, they which run at 54 Mb/s, and they're not supported. Again, that may have changed by the time you read this. Like 802.11b, they run in the 2.4 GHz band.
Most current cards are 802.11b and run at up to 11 Mb/s. We'll concentrate on them in the rest of this section. They operate in the 2.4 GHz band, which is shared with a number of other services, including some portable telephones and microwave ovens. This kind of portable telephone can completely disrupt a wireless network. Interference and range are serious issues: wireless networks are generally not as reliable as wired networks.
Wireless cards can operate in up to three different modes:
- Normally, they interoperate with an access point, also called a base station. The base station is normally connected to an external network, so it also doubles as a gateway. Unlike Ethernets, however, all traffic in the network goes via the base station. This arrangement is called a Basic Service Set or BSS.
Networks can have multiple base stations which are usually interconnected via a wired Ethernet. If the machine with the wireless card moves around, the base stations negotiate with the machine to decide which base station handles the card. In this manner, the machines can cover large distances without losing network connection. This arrangement is called an Extended Basic Service Set or EBSS.
This mode of operation, with or without an EBSS, is called managed mode, infrastructure mode or BSS mode.
- In smaller networks, the cards can interact directly. This mode of operation is called peer-to-peer mode, ad-hoc mode or IBSS mode (for Independent Basic Service Set).
- Finally, some cards support a method called Lucent demo ad-hoc mode, which some BSD implementations used to call ad-hoc mode. But it's not the same as the previous method, and though the principle is the same, they can't interoperate. This mode is not standardized, and there are significant interoperability issues with it, so even if it's available you should use IBSS mode.
How wireless networks coexist
Wireless networks have a number of issues that don't affect Ethernets. In particular, multiple networks can share the same geographical space. In most large cities you'll find that practically the entire area is shared by multiple networks. This raises a number of issues:
- There's only so much bandwidth available. As the number of networks increase, the throughput drops.
There's no complete solution to this problem, but it's made a little easier by the availability of multiple operating frequencies. Depending on the country, 802.11b cards can have between 11 and 14 frequency channels. If your area has a lot of traffic on the frequency you're using, you may be able to solve the problem by moving to another frequency. That doesn't mean that this many networks can coexist in the same space: as the name spread spectrum indicates, the signal wanders off to either side of the base frequency, and in practice you can use only three or four distinct channels.
- Cards on a given network need to have a way to identify each other. 802.11 solves this issue by requiring a network identification, called a Service Set Identifier or SSID. All networks have an SSID, though frequently base stations will accept connections from cards that supply a blank SSID. SSIDs don't offer any improvement in security: their only purpose is identifying the network.
- Cards on a given network need to protect themselves against snooping by people who don't belong to the network. The 802.11 standard offers a partial solution to this issue by optionally encrypting the packets. We'll look at this issue below.
Encryption
As mentioned above, security is a big issue in wireless networks. The encryption provided is called Wired Equivalent Privacy or WEP, and it's not very good. Everybody connecting to the network needs to know the WEP key, so if anybody loses permission to access the network (for example, when changing jobs), the WEP keys need to be changed, which is a serious administrative problem. In some cases it's completely impractical: if you want to access a wireless network in an airport or a coffee shop (where they're becoming more and more common), it's not practical to use a WEP key. In fact, nearly all such public access networks don't use encryption at all.
As if that weren't bad enough, the WEP algorithm is flawed. Depending on the circumstances, it can take less than 10 minutes to crack it. Don't trust it.
So how do you protect yourself? The best solution is, of course, don't use wireless networks for confidential work. If you have to use a wireless network, make sure that anything confidential is encrypted end-to-end, for example with an ssh tunnel, which we'll look at on page 424.
The reference network
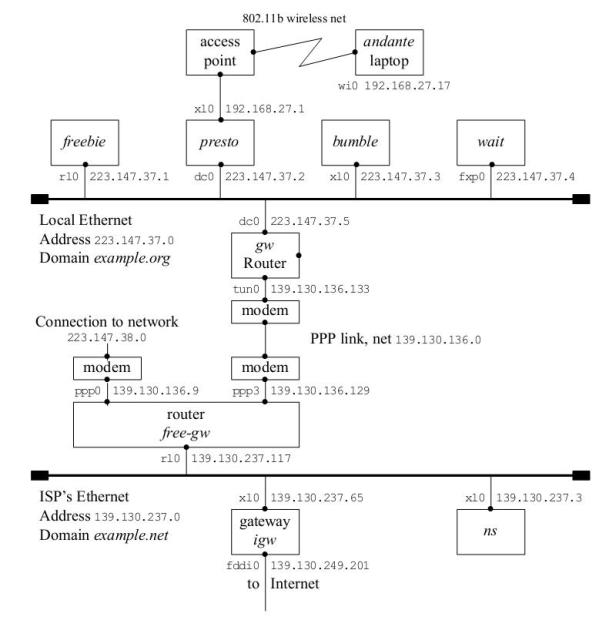
One of the problems in talking about networks is that there are so many different kinds of network connection. To simplify things, this book bases on one of the most frequent environments: a number of computers connected together by an Ethernet LAN with a single gate way to the Internet. Figure 16-8 shows the layout of the network to which we will refer in the rest of this book.
This figure contains a lot of information, which we will examine in detail in the course of the text:
- The boxes in the top row represent the systems in the local network example.org: freebie, presto, bumble, and wait.
- The line underneath is the local Ethernet. The network has the address 223.147.37.0. It has a full 256 addresses ("Class C"), so the network mask is 255.255.255.0.
- The machines on this Ethernet belong to the domain example.org. Thus, the full name of bumble is bumble.example.org. We'll look at these names in "The Domain Name Service" .
- The connections from the systems to the Ethernet are identified by two values: on the left is the interface name, and on the right the address associated with the interface name.
- Further down the diagram is the router, gw. It has two interfaces: dc0 interfaces to the Ethernet, and tunO interfaces to the PPP line to the ISP. Each interface has a different addresses.
- The lower half of the diagram shows part of the ISP's network. It also has an Ethernet, and its router looks very much like our own. On the other hand, it interfaces to a third network via the machine igw. To judge by the name of the interface, it is a FDDI connection—see page 285 for more details.
- The ISP runs a name server on the machine ns, address 139.130.237.3.
- The ends of the Ethernets are thickened. This represents the terminators required at the end of a coaxial Ethernet. We talked about them on page 287. In fact this network is a 100 Mb/s switched network, but they are still conventionally represented in this form. You can think of the Ethernets as the switches that control each network.
- presto has a wireless access point connected to it. The diagram shows one laptop, andante, connected via a NAT interface.