| Узбекистан, Бухара, Бухарский институт высоких технологий, 2013 |
Networks and the Internet
In this part of the book we'll look at the fastest-growing part of the industry: networks, and in particular the Internet.
The industry has seen many different kinds of network software:
- Years ago, the CCITT started a group of recommendations for individual protocols. The CCITT is now called the ITU-T, and its data communications recommendations have not been wildly successful. The best known is probably recommendation X.25, which still has a large following in some parts of the world. An X.25 package was available for FreeBSD, but it died for lack of love. If you need it, you'll need to invest a lot of work to get it running.
- IBM introduced their Systems Network Architecture, SNA, decades ago. It's still going strong in IBM shops. FreeBSD has minimal support for it in the Token Ring package being developed in FreeBSD-CURRENT.
- Early UNIX machines had a primitive kind of networking called UUCP, for UNIX to UNIX Copy. It ran over dialup phone lines or dedicated serial connections. System V still calls this system Basic Networking Utilities, or BNU. Despite its primitiveness, and despite the Internet, there are still some applications where UUCP makes sense, but this book discusses it no further.
- The Internet Protocols were developed by the US Defense Advanced Research Projects Agency (DARPA) for its ARPANET network. The software was originally developed in the early 80s by BBN and the CSRG at the University of California at Berkeley. The first widespread release was with the 4.2BSD operating system—the granddaddy of FreeBSD. After the introduction of IP, the ARPANET gradually changed its name to Internet.
The Internet Protocol is usually abbreviated to IP. People often refer to it as TCP/IP, which stands for Transmission Control Protocol/Internet Protocol. In fact, TCP is just one of many other protocols that run on top of IP. In this book, I refer to the IP protocol, but of course FreeBSD includes TCP and all the other standard protocols. The IP implementation supplied with FreeBSD is the most mature technology you can find anywhere, at any price.
In this part of the book, we'll look only at the Internet Protocols. Thanks to its background, FreeBSD is a particularly powerful contender in this area, and we'll go into a lot of detail about how to set up and operate networks and network services. In the chapters following, we'll look at:
- How the Internet works, which we'll look at in the rest of this chapter.
- How to set up local network connections in "Configuring the local network" , Configuring the local network.
- How to select an Internet Service Provider in "Connecting to the Internet" , Connecting to the Internet.
- How to use the hardware in "Serial communications" , Serial communications.
- How to use PPP in "Configuring PPP" , Configuring PPP.
- How to set up domain name services in "The Domain Name Service" , The Domain Name Service.
- How to protect yourself from intruders in "Firewalls, IP aliasing and proxies" , Fire walls, IP aliasing and proxies. This chapter also describes proxy servers and Network Address Translation.
- How to solve network problems in "Network debugging" , Network debugging.
- Most network services come in pairs, a client that requests the service, and a server that provides it. In "Basic network access: clients" , Basic network access: clients we'll look at the client side of the World Wide Web ("web browser"), command execution over the net, including ssh and telnet, copying files across the network, and mounting remote file systems with NFS.
- In "Basic network access: servers" , Basic network access: servers we'll look at the server end of the same services. In addition, we'll look at Samba, a server for Microsoft's Common Internet File System, or CIFS.
- Electronic mail is so important that we dedicate two chapters to it, "Electronic mail: clients" , Electronic mail: clients and "Electronic mail: servers" , Electronic mail: servers.
The rest of this chapter looks at the theoretical background of the Internet Protocols and Ethernet. You can set up networking without understanding any of it, as long as you and your hardware don't make any mistakes. This is the approach most commercial systems take. It's rather like crossing a lake on a set of stepping stones, blindfolded. In this book, I take a different approach: in the following discussion, you'll be inside with the action, not on the outside looking in through a window. It might seem unusual at first, but once you get used to it, you'll find it much less frustrating.
Network layering
One of the problems with networks is that they can be looked at from a number of different levels. End-users of PCs access the World Wide Web (WWW), and often enough they call it the Internet. That's just plain wrong. At the other end of the scale is the Link Layer, the viewpoint you'll take when you first create a connection to another machine.
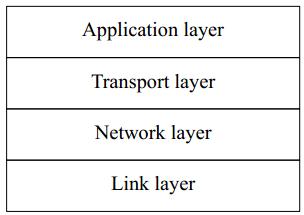
Years ago, the International Standards Organization came up with the idea of a seven-layered model of networks, often called the OSI reference model. Why OSI and not ISO? OSI stands for Open Systems Interconnect. Since its introduction, it has become clear that it doesn't map very well to modern networks. W. Richard Stevens presents a better layering in TCP/IP Illustrated, Volume 1, page 6, shown here in Figure 16-1 .
We'll look at these layers from the bottom up:
- The Link layer is responsible for the lowest level of communication, between machines that are physically connected. The most common kinds of connection are Ethernet and telephone lines. This is the only layer associated with hardware.
- The Network layer is responsible for communication between machines that are not physically connected. For this to function, the data must pass through other machines that are not directly interested in the data. This function is called routing. We'll look at how it works in "Configuring the local network" .
- The Transport Layer is responsible for communication between any two processes, regardless of the machines on which they run.
- The Application Layer defines the format used by specific applications, such as email or the Web.
The link layer
Data on the Internet is split up into packets, also called datagrams, which can be transmitted independently of each other. The link layer is responsible for getting packets between two systems that are connected to each other. The most trivial case is a point-to-point network, a physical connection where any data sent down the line arrives at the other end. More generally, though, multiple systems are connected to the network, as in an Ethernet. This causes a problem: how does each system know what is intended for it?
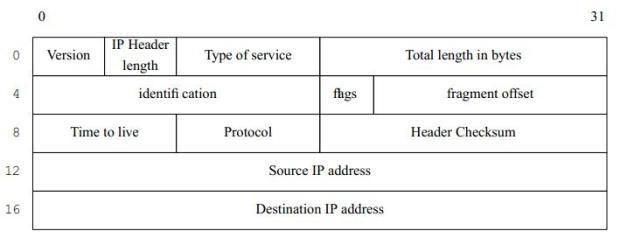
IP solves this problem by including a packet header in each IP packet. Consider the header something like the information you write on the outside of a letter envelope: address to send to, return address, delivery instructions. In the case of IP, the addresses are 32-bit digits that are conventionally represented in dotted decimal notation: the value of each byte is converted into decimal. The four values are written separated by dots. Thus the hexadecimal address 0xdf932501 would normally be represented as 223.147.37.1.
As we will see in "Network debugging" , it makes debugging much easier if we understand the structure of the datagrams, so I'll show some of the more common ones in this chapter. Figure 16-2 shows the structure of an IP header.
We'll only look at some of these fields; for the rest, see TCP/IP Illustrated, Volume 1.
- The Version field specifies the current version of IP. This is currently 4. A newer standard is IPv6, Version number 6, which is currently in an early implementation stage. IPv6 headers are very different from those shown here.
- The time to live field specifies how many times the packet may be passed from one system to another. Each time it is passed to another system, this value is decremented. If it reaches 0, the packet is discarded. This prevents packets from circulating in the net for ever as the result of a routing loop.
- The protocol specifies the kind of the packet. The most common protocols are TCP and UDP, which we'll look at in the section on the network layer.
- Finally come the source address, the address of the sender, and the destination address, the address of the recipient.
The network layer
The main purpose of the network layer is to ensure that packets get delivered to the correct recipient when it is not directly connected to the sender. This function is usually called routing.
Imagine routing to be similar to a postal system: if you want to send a letter to somebody you don't see often, you put the letter in a letter box. The people or machines who handle the letter look at the address and either deliver it personally or forward it to somebody else who is closer to the recipient, until finally somebody delivers it.
Have you ever received a letter that has been posted months ago? Did you wonder where they hid it all that time? Chances are it's been sent round in circles a couple of times. That's what can happen in the Internet if the routing information is incorrect, and that's why all packets have a time to live field. If it can't deliver a packet, the Internet Protocol simply drops (forgets about) it. You may find parallels to physical mail here, too.
It's not usually acceptable to lose data. We'll see how we avoid doing so in the next section.